By: Mosiur Rahaman, International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, mosiurahaman@gmail.com
Abstract
The introduction of the digital era has seen a rapid and significant rise in phishing assaults, leading to the necessity for immediate advancements in cybersecurity protocols. Deep learning has become a fundamental tool in addressing these dangers because it can uncover complex patterns in data that older methods may miss. This study conducts a thorough investigation of the latest deep learning algorithms used in phishing detection, offering a comprehensive overview of the present status of the field. We analyze different architectures, assess their effectiveness, and examine how they may be incorporated into current cybersecurity mechanisms.
Keywords: Phishing detection, Deep learning, Cybersecurity
1. Introduction
Phishing attacks, wherein malicious parties masquerade as trustworthy entities to extract sensitive information, pose significant risks to individuals and organizations alike. As phishing techniques evolve, becoming more sophisticated, so too must our methods for detecting them[1]. Deep learning offers promising advancements in this arms race, leveraging complex models to detect and neutralize phishing attempts before they reach their targets [2].
2. Modern Deep Learning Techniques for Phishing Detection
The application of deep learning to phishing detection encompasses various novel architectures, each with distinct capabilities in identifying phishing content. This section examines various approaches, offering an understanding of their operations and the benefits they offer in comparison to each other. Figure 1 Shows complete framework for phishing detection.
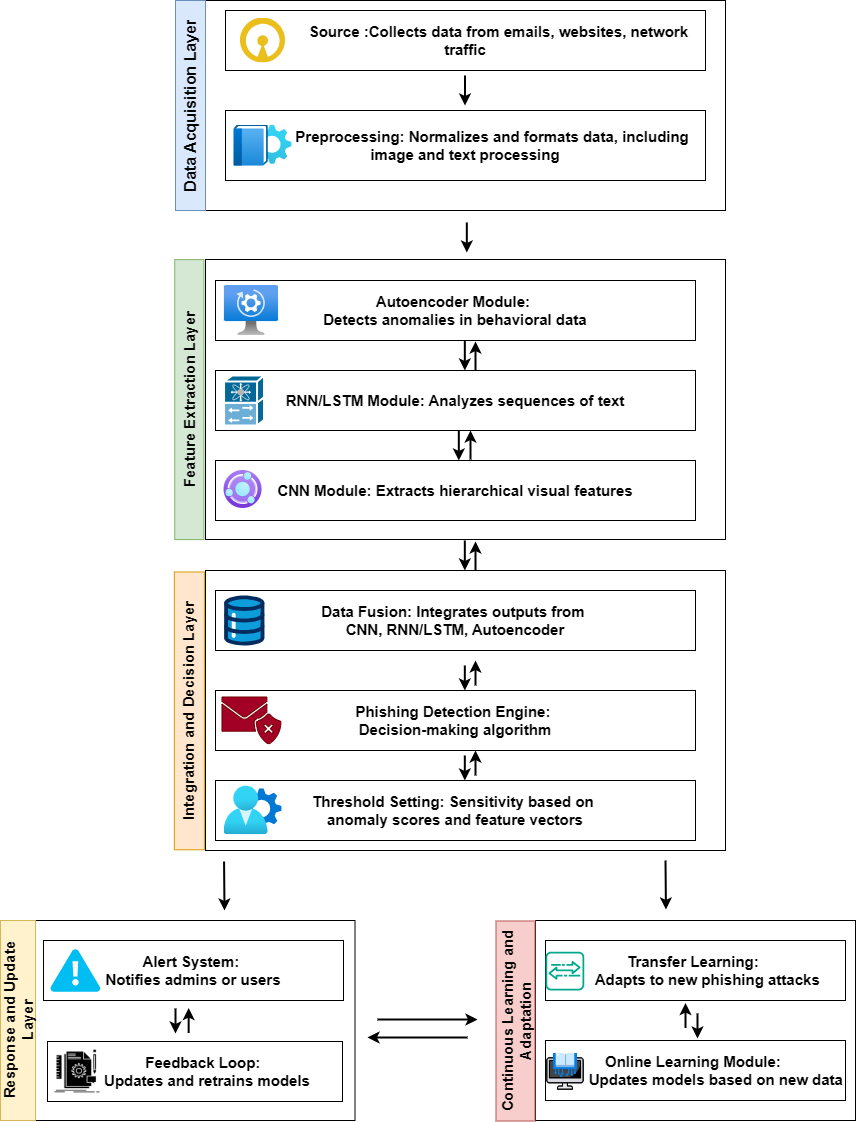
2.1 Convolutional Neural Networks (CNNs)
Convolutional Neural Networks (CNNs) excel in detecting image-based phishing, which refers to phishing attempts that employ misleading logos or website designs. CNNs can accurately differentiate between real and fraudulent websites by extracting hierarchical features from input photos. Studies have demonstrated that Convolutional Neural Networks (CNNs) may achieve impressive levels of accuracy when it comes to detecting phishing URLs that are concealed within images, which is a frequently employed strategy in advanced phishing schemes [3].
2.2 Recurrent Neural Networks (RNNs) and Long Short-Term Memory Networks (LSTMs)
RNNs and their derivative, LSTMs, have demonstrated usefulness in handling textual data, including URLs and phishing emails. These models demonstrate exceptional performance in handling sequential data, acquiring knowledge of interconnections and patterns throughout extended sequences commonly found in harmful URLs or email content. Recent research emphasizes the superior performance of Long Short-Term Memory (LSTM) models compared to typical machine learning techniques. This is due to the LSTM’s capacity to retain significant information across long sequences, which is essential for detecting small indicators of phishing [4].
2.3 Autoencoders
Autoencoders are largely utilized in phishing detection for the purpose of anomaly detection. They are trained to compress and decompress normal traffic or user behavior, identifying anomalies that may suggest potential phishing efforts. This unsupervised learning technique is advantageous in dynamic contexts with continuously shifting phishing tactics, when there is a lack of labelled data, or it quickly becomes outdated [5].
3. Incorporation of Deep Learning Models into Cybersecurity Systems
When incorporating deep learning models into current cybersecurity systems, there are various factors to consider, ranging from choosing the appropriate model to implementing deployment tactics.
3.1 Model Selection and Training
When selecting the appropriate model, it is important to consider the distinct attributes of the phishing data, such as whether it is in text or image format, as well as the computing resources that are accessible. To train these models effectively, a large dataset is necessary. This dataset should include labelled examples of both phishing and legitimate occurrences [6]. Due to the ever-changing nature of phishing attempts, it is necessary to continually update these datasets to incorporate new phishing strategies.
3.2 Challenges in Implementing
Deploying deep learning models in real-time applications presents difficulties, mainly because to the processing requirements of these models and the necessity for immediate responsiveness. Possible solutions involve the implementation of simplified models or the utilization of model distillation techniques to generate lighter models that maintain the effectiveness of their more intricate counterparts [7].
3.3 Continuous Learning and Adaptation
Due to the dynamic and ever-changing nature of phishing attempts, it is important for models to consistently acquire knowledge from fresh data. Methods such as online learning or transfer learning can be used to regularly update the models without the requirement of starting the training process from the beginning. This helps to keep the models up-to-date and effective throughout time [8].
4. Conclusion
Deep learning has significantly advanced phishing detection, offering tools that are both powerful and adaptable. However, challenges remain in terms of integration, real-time application, and continuous learning. Future research should focus on these areas, seeking to enhance the deployment of deep-learning models in practical, operational environments while exploring new architectures that could offer even greater detection capabilities.
Future research:
To further the progress of deep learning in the field of phishing detection, it is recommended that future studies investigate hybrid architectures that merge several deep learning techniques, such as Convolutional Neural Networks (CNNs) and Long Short-Term Memory (LSTMs), with the aim of developing strong defense mechanisms. These mechanisms should be seamlessly integrated into comprehensive and efficient cybersecurity frameworks. An additional focus should be placed on streamlining models by employing methods such as cutting and quantization to enable real-time detection on less capable platforms. Furthermore, the utilization of adaptive learning methods, such as incremental and online learning, is crucial to stay updated with the ever-changing phishing strategies. Moreover, the incorporation of emerging technologies like quantum computing has the potential to greatly improve the ability to detect phishing attempts. Effective development of these technologies will rely on strategic collaboration among academics, industry, and government authorities. To ensure that these models are both novel and practically adaptable in various operating situations, it is important to use a systematic strategy that involves cycle development, collaborative research, and pilot scalability studies.
Reference:
- A. Aleroud and L. Zhou, “Phishing environments, techniques, and countermeasures: A survey,” Computers & Security, vol. 68, pp. 160–196, Jul. 2017, doi: 10.1016/j.cose.2017.04.006.
- E. A. Aldakheel, M. Zakariah, G. A. Gashgari, F. A. Almarshad, and A. I. A. Alzahrani, “A Deep Learning-Based Innovative Technique for Phishing Detection in Modern Security with Uniform Resource Locators,” Sensors, vol. 23, no. 9, Art. no. 9, Jan. 2023, doi: 10.3390/s23094403.
- O. K. Sahingoz, E. BUBEr, and E. Kugu, “DEPHIDES: Deep Learning Based Phishing Detection System,” IEEE Access, vol. 12, pp. 8052–8070, 2024, doi: 10.1109/ACCESS.2024.3352629.
- P. Krishnamoorthy, M. Sathiyanarayanan, and H. P. Proença, “A novel and secured email classification and emotion detection using hybrid deep neural network,” International Journal of Cognitive Computing in Engineering, vol. 5, pp. 44–57, Jan. 2024, doi: 10.1016/j.ijcce.2024.01.002.
- M. Hdaib, S. Rajasegarar, and L. Pan, “Quantum deep learning-based anomaly detection for enhanced network security,” Quantum Mach. Intell., vol. 6, no. 1, p. 26, May 2024, doi: 10.1007/s42484-024-00163-2.
- A. A. Orunsolu, A. S. Sodiya, and A. T. Akinwale, “A predictive model for phishing detection,” Journal of King Saud University – Computer and Information Sciences, vol. 34, no. 2, pp. 232–247, Feb. 2022, doi: 10.1016/j.jksuci.2019.12.005.
- Y. Wang et al., “A survey on deploying mobile deep learning applications: A systemic and technical perspective,” Digital Communications and Networks, vol. 8, no. 1, pp. 1–17, Feb. 2022, doi: 10.1016/j.dcan.2021.06.001.
- Raj, B., et al. (Eds.). (2023). AI for big data-based engineering applications from security perspectives. CRC Press.
- Arya V. (2023) The Evolution of Phishing Attacks How Machine Learning Keeps Up, Insights2Techinfo, pp.1
- Sharma, P. C., et al. (2023). Secure authentication and privacy-preserving blockchain for industrial internet of things. Computers and Electrical Engineering, 108, 108703.
- A. Khan, K. T. Chui (2021) What is Mobile Phishing and How to Detect it?, Insights2Techinfo, pp.1
- Gupta, B. B., & Nedjah, N. (Eds.). (2020). Safety, Security, and Reliability of Robotic Systems: Algorithms, Applications, and Technologies. CRC Press.
- Deborah, L. J., et al. (2023). Secure Data Management for Online Learning Applications. CRC Press.
- O. Sarker, A. Jayatilaka, S. Haggag, C. Liu, and M. A. Babar, “A Multi-vocal Literature Review on challenges and critical success factors of phishing education, training and awareness,” Journal of Systems and Software, vol. 208, p. 111899, Feb. 2024, doi: 10.1016/j.jss.2023.111899.
Cite As
Rahaman M (2024) Foundations of Phishing Detection Using Deep Learning: A Review of Current Techniques, Insights2Techinfo, pp.1