By: A. Khan, K. T. Chui
Smart phones play a significant role in our lives, because of their compact size; extended battery life, and flexibility, smart phones have grown increasingly popular. Smart phones aren’t just for the youngsters and tech-savvy, but are adopted by individuals of all ages. As the number of people using cell phones grows, so do the security risks associated with smart phones. In recent years, these gadgets have been a favorite target for cybercriminals. “Identity theft”, the stealing of someone’s identity, is one of the most lucrative crimes in recent history [1]. Phishing attacks have swiftly risen in popularity; constitute an immense danger to worldwide internet security. Unfortunately, phishing attacks are among the extremely prevalent and dangerous risks on the web, as cyber criminals attempt to obtain exclusive and monetary information from users through the use of malicious programs or psychological manipulation.
The word “phishing” popped up from the metaphor of “fishing” seeking individuals’ login credentials over the internet. The origin of the term “ph” was based on phone phreaking, which was an extremely prevalent method of attacking telephone networks in the 1970s [2]. In 1996, a gang of hackers coined the term “phishing” for the first time on the Internet when they hijacked “America Online” (AOL) accounts by deceiving unwitting AOL members into giving their login credentials [3]. Smart phone users are at least 3 times quite sensitive to phishing cyber attacks than desktop users, and this susceptibility is due to the tiny display size, absence of identification indications, and discomfort of user input, shifting among apps, habits and inclinations of smart phone owners [4].
In accordance with Anti Phishing Working Group (APWG) 1st quarter report of 2021, January month achieved the highest number i.e. 245771 phishing attacks. The “Business e-mail Compromise” scams (BEC) grow $85000 from $48000 in past 3rd quarter of 2020 [10]. The main motivation behind these attacks is to steal personal information, financial benefit, defamation or fame, and ransom.
Smart phones offer an extensive variety of capabilities to their users, including the ability to make phone calls, send SMS messages, receive emails, download files, play games, and listen to music and videos [5]. A significant number of people have been drawn in by the robust capabilities provided by smart phones. In November 2016, a number of smart phones surpassed number of desktops for the first time, demonstrating a shift in consumer preferences concerning how they access the web nowadays. Attackers are well-aware of this trend and are thus focusing their efforts on smart phone owners rather than desktop users.
Figure 1 will illustrate the life cycle of the phishing process and process is discussed below;
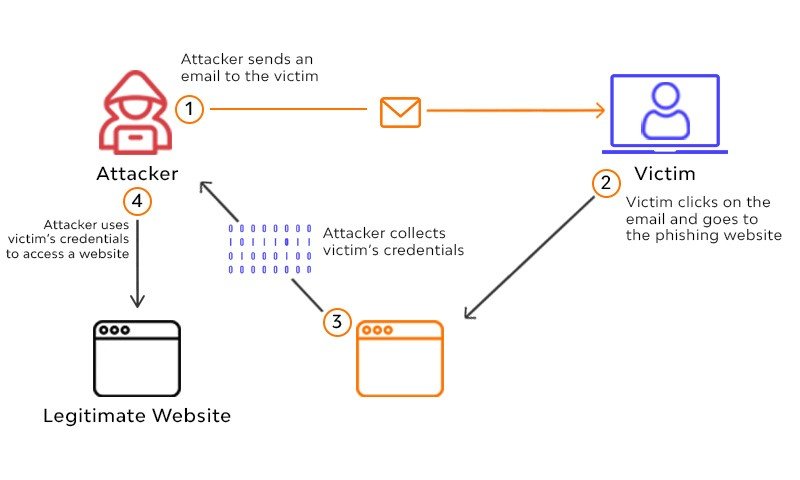
- Planning and Setup Phase: The attackers begin by determining who or what their target is, be it a company, an ordinary person, or an entire nation. After then, it’s up to them to learn more about the company and the people that work there. It’s possible to achieve this by physically travelling to the location or by watching the network traffic coming in and out [6]. The next stage is to set up the assaults by utilizing a viable method, such as a website or email with malicious links that might lead the target to a fraudulent web page.
- Phishing Phase: The next phase is to utilize the gathered email addresses to deliver such spoof emails, e.g., pretending to be some reputable financial institution to the target, asking the user to modify certain information immediately by tapping on some harmful link. Emails can be sent to a group of people or to a particular person inside a company [6].
- Break-in Phase: When a target clicks on a fraudulent link, whether malware is placed upon that system, allowing the attacker to get access and modify the system’s settings, or access privileges are altered to reflect this. Sometimes, it might take you to a bogus website that requests login credentials [6].
- Information Gathering Phase: Upon gaining access to the victim’s machine, the attacker will be able to retrieve the necessary data. If the victim provides his/her login credentials to the attacker, they will have full access to the victim’s account, which may result in financial consequences. Malware assaults now have the potential to provide the attacker remote access to the system, allowing him to steal any information he desires, or to exploit the hacked devices for DDoS attacks or other malicious purposes. Rootkits are used by phishers to disguise their malicious files [6].
- Break-out Phase: To hide their tracks, the phisher creates fake accounts on a variety of popular websites and uses that information to trick others into providing their personal information. As a result, it’s been discovered that they keep tabs on how successful their attack was in order to make improvements on future ones [6].
Mobile phishing attacks can be categorized into various domains depending upon their behavior of acting. For example, social engineering, wireless medium, mobile applications, and malware injection (Ransomware, Trojan, etc.) are the main techniques that can be hazardous to mankind and their identity. The taxonomy of mobile phishing attack schemes is depicted in Figure 2;
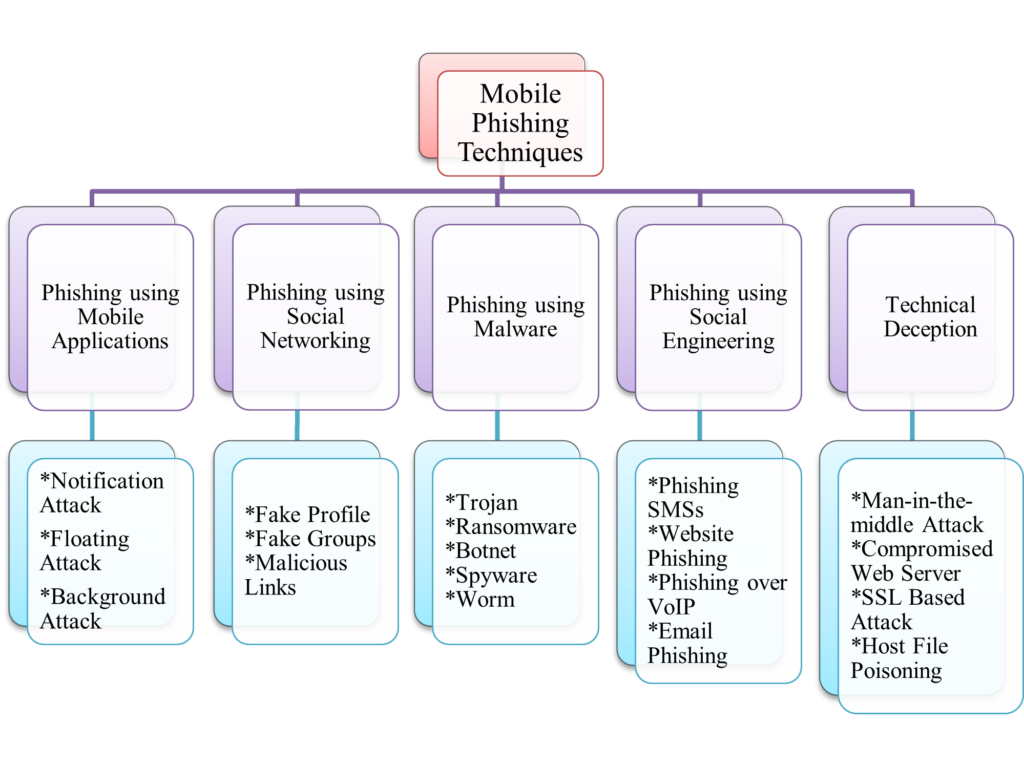
As there are numerous types of phishing attacks present in the literature, to tackle with those malicious phishing attacks some approaches are also designed. In this section, we will describe in brief some of the approaches to identify and tackle those attacks.
- User Education: The term “user education” describes to the process of informing and educating web users concerning phishing. Education-based initiatives provide online data on the dangers of such assaults and how to avoid them. Some techniques additionally offer consumers online training and assessment [7].
- Software Based Defense Approaches
- Network Level Protection: This strategy prevents specific IP address or domain names from connecting to the network. DNSBLs rely on the DNS protocol and are produced and updated on a regular basis by monitoring network traffic [8].
- Authentication Mechanism: This method verifies that the email was delivered using a legitimate route and domain name, and it may be used at both the client and domain level. These methods improve the safety of email correspondence [8].
- Client Side Tools: Various more methods include domain verification, URL analysis, and so forth. As a result of this, these solutions also rely on phishing detection techniques such as blacklisting and white listing, which keep track of known fraudulent or genuine sites and update the list accordingly. One of these methods’ shortcomings is that it cannot identify a zero-day cyber attack [8-10].
- Server Side Tools: In order to combat zero-day assaults, these solutions rely on information classification techniques [8]. Using machine learning approaches, these filters may be divided into four groups:
- Based on Machine Learning Techniques
- Based on Data Mining Techniques
- Based on Soft Computing Techniques
- Multi Layered Phishing Detection Techniques
References
[1] Hong, J. (2012). The state of phishing attacks. Communications of the ACM, 55(1), 74-81.
[2] Wu, M., Miller, R. C., & Garfinkel, S. L. (2006, April). Do security toolbars actually prevent phishing attacks?. In Proceedings of the SIGCHI conference on Human Factors in computing systems (pp. 601-610).
[3] Garera, S., Provos, N., Chew, M., & Rubin, A. D. (2007, November). A framework for detection and measurement of phishing attacks. In Proceedings of the 2007 ACM workshop on Recurring malcode (pp. 1-8).
[4] Jakobsson, M. (2005, February). Modeling and preventing phishing attacks. In Financial Cryptography (Vol. 5).
[5] Gupta, B. B., Tewari, A., Jain, A. K., & Agrawal, D. P. (2017). Fighting against phishing attacks: state of the art and future challenges. Neural Computing and Applications, 28(12), 3629-3654.
[6] Goel, D., & Jain, A. K. (2018). Mobile phishing attacks and defence mechanisms: State of art and open research challenges. Computers & Security, 73, 519-544.
[7] Ramzan, Z. (2010). Phishing attacks and countermeasures. Handbook of information and communication security, 433-448.
[8] Basnet, R., Mukkamala, S., & Sung, A. H. (2008). Detection of phishing attacks: A machine learning approach. In Soft computing applications in industry (pp. 373-383). Springer, Berlin, Heidelberg.
[9] Gupta, B. B., & Jain, A. K. (2020). Phishing attack detection using a search engine and heuristics-based technique. Journal of Information Technology Research (JITR), 13(2), 94-109.
[10] Almomani, A., et al. (2013). Phishing dynamic evolving neural fuzzy framework for online detection zero-day phishing email. arXiv preprint arXiv:1302.0629.
Cite this article:
A. Khan, K. T. Chui (2021) What is Mobile Phishing and How to Detect it?, Insights2Techinfo, pp.1
Very good and useful article on Phishing!
Thank you
Nice work 👏
Thank you for your support
Very informative and interesting work
Thank you
Very informative!
Thank you
Very Informative Work!
Thank you
Very useful and informative article