By: Khushboo Kumari
Social media threat is an important topic to talk about. As social media has created a new platform for communication and interaction, and become a part of our social life that helps us to communicate with others. We all know the coming of social media platforms like Facebook, Twitter, and WhatsApp brought a very big change in how we use the internet for personal and professional purposes. Social media play an important role in modern-day communication [1]. But it is easy for hackers/attackers to get a hold of the user information if the user is not careful about the security. This is very common because people are not careful about it like using the password which is very common as the name of the family member or some familiar place. Downloading or opening the file which contains the malware without conforming to the sender identity. There are ways to prevent these threats like using the algorithms tool which can help to detect the threats. If we see the history of social media we find that attack on social media is done on a big scale, not like Facebook 2007, Facebook, MySpace et al., 2010, Facebook, 2014, and the recent attack on Facebook in 2021. So we can say that there is always a possibility that attackers can attack and get a hold of the user-sensitive information.

Threat on online social media
Multimedia content threats
People share the data like photos, videos, interests, activities, and others. Multimedia data is a type of this data sharing. Users use high resolution for sharing photos and others. But using the advancement in the multimedia technique user location, face recognition, etc. increases the chance of chance to illegally utilize the items. Multimedia content threats are Sharing the ownership, Manipulating the multimedia content, Steganography, Metadata, Exposing the content on multimedia, Sharing the links of multimedia content, Static links, Transparency of data centers, Video conference, Tagging, Disclosing the unauthorized data [1, 2].
Traditional Threats
Traditional threats are unique and include different types of attack techniques, like phishing, malware, identity thief, viruses for obtaining the user’s sensitive information. User sensitive information is very useful for an attacker, like attacker can get hold of other confidential information, like security number of the user used on social media, id for login and its password, and account details for the bank. After an attacker obtains the user information, they can use the data to commit a different types of crimes and serious attacks, like phishing and stealing the identity of the user. The traditional threat used by the attacker is Spamming, De-anonymization attack, Clickjacking, Inference, Cloning the profile, Sybil attack and creating a fake profile, Phishing, Malware [2].
Social threats
In online social media attackers can use the social relationship feature and interact with different kinds of users, like minors, employees of corporations. An attacker can have several motives like blackmailing, cyber harassment, and spying. The various social threats are Cyberbullying and cyber-grooming, Cyberstalking, Corporate espionage [3, 4].

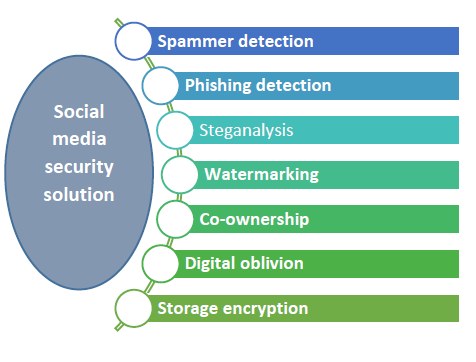
Social media security solution
Threat on social media increase as the use of social media increases. To prevent these threats there are algorithms given that protect the user data. And there are other solutions for detecting and preventing the threat [1, 5-7].
Watermarking is used for superimposing a logo or text on top of a document or image file. This process provides copyright protection and marketing of digital works.
Co-ownership in this multiple users have co-owned data and every user applies their privacy policies on that co-owned data.
Steganalysis on social media there are many malicious information are present. Steganalysis is used to find this malicious information.
Digital oblivion is used to prevent attackers to get access on user-sensitive information after the expiration time of the data.
Storage encryption is used for efficiently storing and recovering user information without exposing any sensitive information to a third party.
Malware detection is used if there is malware propagation present in the social media.
Sybil defense and fake profile detection there are many tools and techniques for detecting fake profiles and providing defense against the Sybil attacks. These methods either depend on the social graphs by performing the limited amount of arbitrary walks or on the random routes concept.
Phishing detection is are anti-phishing methods that find and prevent phishing attack. Machine learning techniques are used in these methods [8].
Spammer detection is used to extract the feature set which separates legitimate and spam users and supply that extracted feature set to different machine learning classifier models to identify the activities which is inappropriate.
Issues
- Misuse the Identity– in these type of attack attacker impersonate the identity of another user which result in identity theft. By using this they can gain the access on user personal information.
- Using 3rd Party Applications– There are applications which ask for permission from user for accessing sensitive information of different type of apps. Like access on camera, gallery etc. And some of these applications may contain malware which will be downloaded on the user’s personal device without their consent.
- Trust on the Operators of Social Networking Sites– when user upload or post on the social networking sites, the upload and post are available to operators of the social networking sites. If operators want to save account data, they can save it even after deletion and use it for getting user information.
- DDoS Attacks: DDoS attacks are performed by attackers to exploit the availability of information on the social media [9-11].
- Legal Issues– There are cases where user post contents which can displease to any individual, community or even a country. So if someone invading someone’s privacy and leaked these confidential information, there can be legal risk associated to it.
- Viruses, Phishing Attacks and Malwares– when we use social media there we always get some ads. From those ads, these types of attack find their way onto the user device. After finding their way to the device, they start gaining access to the network, though these attacker can get hold of sensitive information by using spam mails [12].
- Privacy of user Data– User post or upload their information on social media which can become cause for the privacy related issue because attacker can gain access to the data using various method.
Challenges
- Phishing Attacks
- Identity Federation Challenges
- Malwares
- Click Jacking Attacks
Research direction
For making social media more secure, we can use cryptography. In cryptology, we can use different types of algorithms to make social media more secure like RSA algorithms, AES, end-to-end encryption, digital signature, etc. But still, we need to work on this area to give user data more security.
Conclusion
In this overview, we have given the different types of attacks that can happen to a user on social media. And different type of solution which is already available to prevent these type of attack.
We can use different types of algorithms like RSA, AES, Digital signature, etc. to stop the attacker to get a hold of the user sensitive information
References
- Rathore, S., Sharma, P. K., Loia, V., Jeong, Y. S., & Park, J. H. (2017). Social network security: Issues, challenges, threats, and solutions. Information sciences, 421, 43-69.
- S. Rathore, P. Sharma, V. Loia, et al. Social network security: Issues, challenges, threats, and solutions.
- Barinka, A. (2017). Bad Day for Newsweek, Delta Amid Social-Media Hackings.
- El Asam, A., & Samara, M. (2016). Cyberbullying and the law: A review of psychological and legal challenges. Computers in Human Behavior, 65, 127-141.
- Gupta, S. S., Thakral, A., & Choudhury, T. (2018, June). Social Media Security Analysis of Threats and Security Measures. In 2018 International Conference on Advances in Computing and Communication Engineering (ICACCE) (pp. 115-120). IEEE.
- Zhang, Z., Sun, R., Zhao, et al. (2017). CyVOD: a novel trinity multimedia social network scheme. Multimedia Tools and Applications, 76(18), 18513-18529.
- Gupta, S., et al. (2018). Robust injection point-based framework for modern applications against XSS vulnerabilities in online social networks. International Journal of Information and Computer Security, 10(2-3), 170-200.
- Khan, A., & Chui, K. T. What is Mobile Phishing and How to Detect it?. Insights2Techinfo, pp.1
- Chhabra, M., et al. (2013). A novel solution to handle DDOS attack in MANET. Journal of Information Security Vol. 4 No. 3 (2013) , Article ID: 34631 , 15 pages DOI:10.4236/jis.2013.43019
- Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE communications surveys & tutorials, 15(4), 2046-2069.
- Tripathi, S., et al. (2013). Hadoop based defense solution to handle distributed denial of service (ddos) attacks. Journal of Information Security, Vol. 4 No. 3 (2013) , Article ID: 34629 , 15 pages.
- R. S. Pal (2021) Phishing Attack in Modern World, Insights2techinfo, pp.1
Cite this paper as:
Khushboo Kumari (2021) Online social media threat and It’s solution, Insights2Techinfo, pp.1
Also read:
- 1.2 Million Accounts of GoDaddy got Hacked
- Operating System Security and Significance of Logging
- Captcha Improvement: Security from DDoS Attack
- Phishing Attack in Modern World