By: R. S. Pal
While the size and sophistication of cybersecurity threats continue to rise, social engineering techniques remain popular. some of the easiest and most successful methods of gaining access to information that is sensitive or confidential. The United States Computer Emergency Readiness Team (US-CERT) describes phishing as a type of social engineering that involves the use of e-mails or other electronic communications. Harmful websites attempt to get personal information from an individual person or corporation by impersonating a reputable entity or a thing [1].
Phishing websites [2] [3] is one such area where administrators want innovative approaches and algorithms to safeguard inexperienced visitors from being abused. Phishing is a type of fraud that involves attempting to obtain our personal information through the use of emails [4][5]. These phishing emails typically appear from reputable sources and attempt to get sensitive information such as passwords, bank account information, or even Social Security numbers. These assaults frequently originate from sites where we do not even have an account [6].
There are display limitations that may be used to conceal the URL bar. Furthermore, owing to these limits, mobile browsers do not display When showing a website, the favorites bar appears. It is often used. It is tough for people to tell the difference between phone and real user interfaces (UI), and since they are unable to view them They may tumble into the abyss of bookmarks and URLs. Bogus user interfaces Furthermore, mobile users grow acquainted with submitting their personal information on many mobile devices’ settings. Indeed, “40% of mobile users type passwords into their devices.”[7]
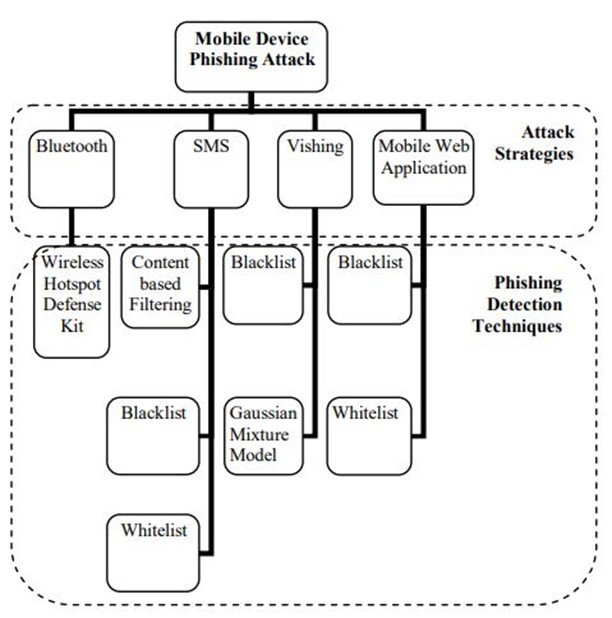
Taxonomy of phishing attack
The goal of phishing taxonomy development is to provide a basic understanding of phishing attacks and how to identify them on mobile devices (Fig. 1). The Attack Strategies and Phishing Detection Techniques are the main components of the proposed taxonomy. All of these variables will be used to create a phishing detection taxonomy for mobile devices in the proposed taxonomy. This can be used as an alternative to learning how to put together a phishing detection framework for a mobile device. Foozy, Ahmad, and Abdollah [8] et. al. discussed the taxonomy of phishing attacks in their paper. The main elements are –
- Mobile Device Phishing Detection Taxonomy
- Attack Strategies
- Phishing Detection Techniques
As a social engineering assault, phishing must be a countermeasure and different defense, although many alternative ways to detect phishing attacks on mobile devices have been proposed. Since Mobile devices are one of today’s most important current technologies, this attack has transformed mobile device tactics.
The most common types of Bluetooth attacks
BlueSmacking – Attackers use BlueSmacking mostly on edge devices that have Bluetooth-enabled settings. It is a type of DDOS attack. As we know it occurs when a target gets overflowed by the data packet than expected. so, as a result when the target machine gets overflowed it generally shuts. denial-of-service attacks might seem non-lethal when compared to other types of cyber-attacks but most of the time it is used as a diversion and attackers might focus on carrying out some other attacks.
Bluejacking – When Bluetooth is used for hijacking purposes it is known as BlueJacking. it is the basic method of the attackers to send spam messages to the victim’s device. As the Bluetooth has a very low range i.e., approximately 10 m so generally the attacker is closer to us than we expect. Sometimes it is also seen that then the attackers knowingly planted some devices on-road or in some crowded place and their infected device uses Bluetooth to spread the spam messages. Now this message as the name suggests is used for a phishing attack. Phishing is a term used in cyber security to point out that the attacker is trying to trick the user by showing him some trusted the site more like a clone of it and trying to steal their credentials. The phishing attack can happen on banking sites on social media or even nowadays in e-commerce sites. This message has a hyperlink option which is made as a lookalike of some original trusted URL for these sites and whenever the victim opens this link and enters the credentials the attacker can easily get it.
BlueBugging – There is another type of Bluetooth attack known as blue bugging. it is used to create a backdoor in the victim’s phone or any age device here which uses Bluetooth to create such a backdoor. Now backdoor can be very dangerous as the attack or any malicious outsider can easily gain access to the victim’s device for sensitive teeth. These back those are also used to spy on someone. This can be very dangerous as they can even have the victims’ credentials of some banking sites or nowadays as social media is an essential part of people’s life so, the attacker can also exploit that information by spying on them.
Smishing –Smishing is a type of phishing that is carried out by SMS on mobile phones specifically. Nowadays it has become popular among the attackers as more and more people have smartphones or mobile phones and smartphone has become cheap. so, it is affordable and as a result, the cybercriminals are also actively looking to exploit. The attacker sends a text message to the victim’s phone, this text message is either has some link ok or tried to trick the user somehow. Now there are two possibilities when the user opens the link.
- The user opens the link and its phishing site lookalike like the original and cloned. Then user puts his credentials, and the attacker gets what he wants.
- When the user opens the link some Malware or spy software silently downloads into the victim’s machine. Now this gives the attacker a backdoor as now we can easily gain access to the victim’s personal information or maybe corporate data whatever. Research shows that this attack was somehow 98% successful and so it is very dangerous.
Mobile Web-Application
Victims’ Devices can get affected by malicious Applications in various ways. The first one is that the user unknowingly downloaded some infected application which is very well crafted by the attacker. The user might think that the app is free but it is not free and comes with a heavy price that is the security of his machine and give the attacker free access to his machine. In such cases When the source is untrustworthy it is very much possible that the app has the malicious code already added with and wherever the user activates that app the source code starts Working. Sometimes the app can also reside in some trustworthy sources and in that case the user is actually helpless as he can’t even suspect that the app, he downloaded from the trusted source has some malicious link attached. This is the reason that corporate offices use only some registered and pre-approved software in their working machines otherwise if in a big organization somehow one device gets affected then the whole chain off connection might fail. so, it is always better to download applications from trusted sites like Google or Apple their time to time to check the apps and if there is some serious issue, they remove such apps.
Current Phishing attack Detection Solutions
As a social engineering assault, phishing must be a countermeasure and different defense, although many alternative ways to detect phishing attacks on mobile devices have been proposed. Since Mobile devices are one of today’s most important current technologies, this attack has transformed mobile device tactics.
There are many phishing attack detection techniques for mobile devices that have been categorized [9] [10] [11].
- Content-Based Filtering – This technique has exhibited a phishing attack on email successfully. In order to improve the typical mobile device spam filter technique, the combinations of these strategies are necessary because the content of the filtering alone is less effective. Content-based filters can also be separated into rule-based and statistical filters. In this technique, we neutralize Smishing, a type of phishing attack strategy. The advantages of this technique are that it is flexible and the disadvantages are that it is less efficient.
- Visual Based Filtering – herebased on the pictures, blocks, and layout, we compute a visual resemblance between the phishing and authentic pages.
- Black list technique – This technique is used to prevent Smishing, Vishing, and mobile web. The advantage of this technique is that it gives low false positives and also can effectively detect known phishing URLs. But it is not suitable to detect new attacks like -zero-day phishing attacks. It is less efficient to update and verify the attack in the database. So, we can say this technique is inefficient alone to protect users from phishing attacks. It is frequently used as anti-phishing in the toolbar in industries. A warning will be displayed whenever the user enters the blacklist website.
- Whitelist technique – This technique is used to prevent mobile web and Smishing. It is basically the opposite of a blacklist as it has a list of trusted senders. but it failed to detect phishing from a known sender.
- Wireless Hotspot Défense tools – It is used to defend from Bluetooth attacks. It may monitor any change on the ESSID, the access point’s MAC address, the default gateway’s MAC address, and the network’s dramatic signal strength variations. The problem is it needs an expert to review and monitor the network so for a normal user this technique might not be much useful.
- Gaussian mixture model – This technique is used to prepare Vishing. It identifies lies and true statements.
Current Challenges in phishing attack detection
- In content-based Filtering, there is a lack of variety and novelty.Need to capture a significant amount of users’ information, which may lead to regulatory and pricing issues.
- Scalability is a challenge.
- The quality of content-based solutions is only as good as the experts who tag items. Many of these items may require attributes to be assigned, and because attributes can be subjective, the expert can even incorrectly tag them.
- The blacklist-based solution can just identify phishing sites that are on the list yet can’t recognize zero-day phishing assaults that have shown up for a really long time or even hours. It is conceivable that new phishing sites might have as of now taken client accreditations or even lapsed prior to being added to the blacklist.
- Whitelisting can be time-consuming and labor-intensive because only after approving the entity it will be listed. This means that without authorization nothing is allowed in. The disadvantage is that it takes longer as we add new items. So, the productivity can be slow because only after the approval process user can access anything new.
References
[1] N. Lord, “What is a Phishing Attack? Defining and Identifying Different Types of Phishing Attacks”.https://digitalguardian.com/blog/whatphishing-attack-defining-and-identifying-different-types-phishingattacks, 2018.
[2] Ishant Tyagi, “Detection of Phishing Attacks using Machine Learning,” in 5th International Conference on Signal Processing and Integrated Networks (SPIN), 2018.
[3] A. Khan, K. T. Chui (2021) What is Mobile Phishing and How to Detect it?, Insights2Techinfo, pp.1
[4] Khonji, M., Iraqi, Y., & Jones, A. (2013). Phishing detection: a literature survey. IEEE Communications Surveys & Tutorials, 15(4), 2091-2121.
[5] Almomani, A., et al. (2013). A survey of phishing email filtering techniques. IEEE communications surveys & tutorials, 15(4), 2070-2090.
[6] A. Sethi, K. T. Chui, et al (2021), Computer Security. Insights2Techinfo, pp. 1
[7] M. Jakobsson, E. Shi, P. Golle and R. Chow, “Implicit Authentication for Mobile Devices,” Palo Alto Research Center, 2016.
[8] Foozy1 , Rabiah Ahmad2, and Mohd Faizal Abdollah3 ,” Phishing Detection Taxonomy for Mobile Device”, IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 1, No 3, January 2013
[9] H. Shahriar, T. Klintic, and V. Clincy, “Mobile phishing attacks and mitigation techniques,” Journal of Information Security, vol. 6, no. 3, pp. 206–212, 2015.
[10] Jain, A. K. et. al. (2020). Phishing attack detection using a search engine and heuristics-based technique. Journal of Information Technology Research (JITR), 13(2), 94-109.
[11] Almomani, A., et al. (2013). Phishing dynamic evolving neural fuzzy framework for online detection zero-day phishing email. arXiv preprint arXiv:1302.0629.
Cite this article:
R. S. Pal (2021) Phishing Attack in Modern World, Insights2techinfo, pp.1