The development of Internet technologies in recent times has brought a drastic change in the field of medical science. Hospitals and health professionals are changing the traditional text-based patient health record system with new multimedia technologies such as Image, Video, audio. Internet and multimedia-based patient health record systems have been very popular due to their reliability and confidentiality.
Techniques for Patient health record security
There are mainly three types of techniques used by the different organizations for providing protection of patient’s health records against hackers [5], as represented in figure 1.
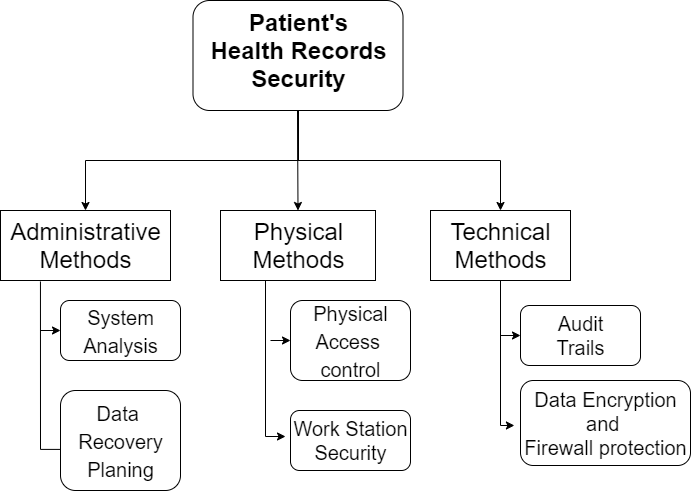
- Administrative methods: In this a central authority mange and implement the security protocols.
- Physical methods: This technique mainly focuses on the physical access of patient’s data.
- Technical methods: In this technique, the protective data sharing methods are developed.
Advantage of Multimedia based Patient health record
The use of the Internet and multimedia in storing patient health records has provided quick access to health records to health professionals around the world. Since electronic health records stay for a long period of time, health professionals are benefitted as they can extract knowledge from these data with several data mining, machine learning, and deep learning techniques. These data can be used in disease prediction and early symptom detection which can greatly improve patient health and cost optimization. Several webs and mobile app-based patient health record systems provide the patient a good visualization and understanding of their health conditions such as blood pressure. These technologies have empowered general consumers to understand diseases in a sophisticated manner. Health professionals are now using techniques such as Medical Imaging which uses images of different diseases such as tumors and strokes. These Images have been very useful for the health professional in understanding diseases better than following the traditional way of disease detection.
Limitations and Solutions of Multimedia Based Patient Health Records
The use of multimedia in the patient health records suffers from the generation of a large amount of data and data management. To cope up with this problem development of a cloud-based system has been very useful. Several novel data mining approaches can be proposed to extract knowledge from these large databases. The bandwidth challenges that the internet faces with volumetric databases can be solved by lossless Image, audio, and video compression techniques. Electronic health record systems give rise to several security problems such as un authorization, confidentiality, denial of services. The PIN-based authentication system can be amplified with a credential-based authentication system. The confidentiality of the health record can be maintained by encrypting data with strong encrypting algorithms. Nowadays blockchain approach has been very applicable to maintain the confidentiality of a health record.
International Standards for the security of Patient Health Records
Because patient health records include sensitive and private information, government authorities devise a variety of methods for gaining access to them. Following is a quick explanation of a few of these rules and regulations:
HIPAA Act
The HIPAA Act [1] became law on August 21, 1996, with the objective of maintaining the security and long-term viability of healthcare data and information flow in the United States. HIPPA act granted security, integrity, and confidentiality to the patient health records. When it comes to creating a safe patient’s health record system, the HIPPA legislation comprises a slew of security standards, administrative regulations, technological specifics, organizational criteria, and regular processes that must be followed [2].
ISO 20000
It was the industry’s first standard for information technology management services, having been released in 2005 and revised in 2011. ISO 20000, is based on the British Standard BS 15000, is split into two components [3].
• The first segment is devoted to the administration of information technology services. It defines guidelines for ensuring the quality of accessible services by standardizing the necessary approach of information operations management.
• The second component contains the guideline standard, which details the methods for service management.
ISO 27000
Information security essential ideas were established and maintained during the development of this standard [4]. This assists in identifying and mitigating serious security risks. ISO 27001 is foundational of the ISO 27000 standard, which focuses on information security services. ISO 27001 is the most widely used information security management standard in the world. It assists organizations in identifying and mitigating present and prospective information security risks. Risk detection and assessment, policy formulation, human resources control, access control, and information security management are all covered by the ISO 27001.
ISO 27799 in the medical sector is a subset of the ISO 27000 standard that is used in the health sector to protect the patients’ health records. The ISO 27001 Information Security Management System does not address the security of health institutions, protected health information, or other risks to the industry.
Research Area in Multimedia Based Patient Health Records
Some of the eminent research areas on this topic include the following:
- Electronic based patient health record system
- Data mining techniques for non-relational health data
- Convolution neural network in Medical Imaging
- Deep learning techniques in patient health records data
- Sensor-based gadgets for health data collection
- Cloud storage for patient health record
- Security issue in the cloud storage
- Security issue in wireless sensor networks.
- Authentication system in smart gadgets
- Confidentiality issue in patient health records.
- Compression technique for non-relational database
- Security issue in the user authentication system
- Dimensionality reduction techniques in Images
- Data transmission problem for volumetric database.
- Denial of service attacks in health record server
- Smart card in the patient health record
- Development of patient-friendly health recording system
- Blockchain techniques in recording patient health data.
- Development of mHealth.
- Data breach problem in the patient health record
References
- Prajesh Chhanabhai, Alec Holt, Inga Huntur, “Consumers, Security and Electronic Health Records”, New Zelland, 2006.
- Par, O. E., & Soysal, E. (2012, August). Security standards for electronic health records. In 2012 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (pp. 815-817). IEEE.
- ISO/IEC 20000 Certification and Implementation Guide, Claire Engle,Gerard Blokdijk,Jackie Brewster, Emereo Publishing, Australia, 2008.
- Information Security Based on ISO 27001/ISO 27002: A Management Guide, Alan Calder, Van Haren Puplishing, NL, 2006.
- Kruse, C. S., Smith, B., Vanderlinden, H., & Nealand, A. (2017). Security techniques for the electronic health records. Journal of medical systems, 41(8), 1-9.
Cite this article:
A.Gaurav (2021) Internet, multimedia and security in patient’s health record, Insights2Techinfo, pp.1
Also read:
- Voice over IP (VoIP)
- Smart Adoption of IoT in COVID-19 Pandemic paves new era of sustainable future world
- Moving Object Detection System: Wi-Vi
- Zero-Shot Temporal Activity Detection
- Virtual Personal Assistant